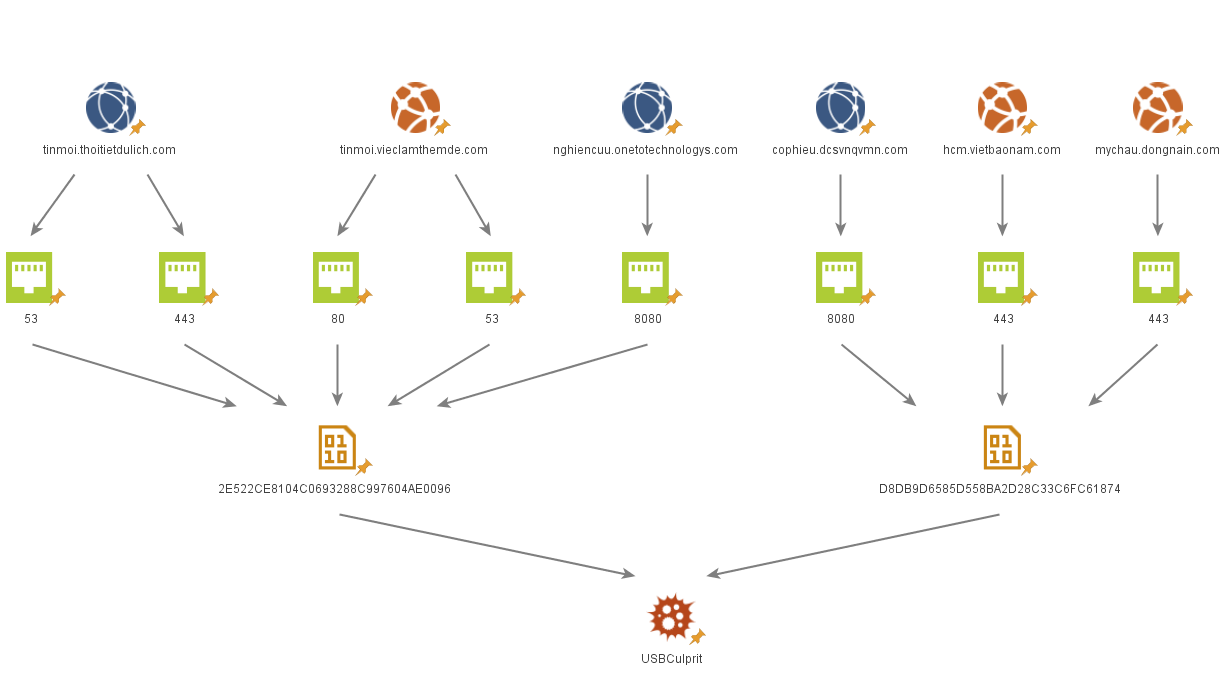
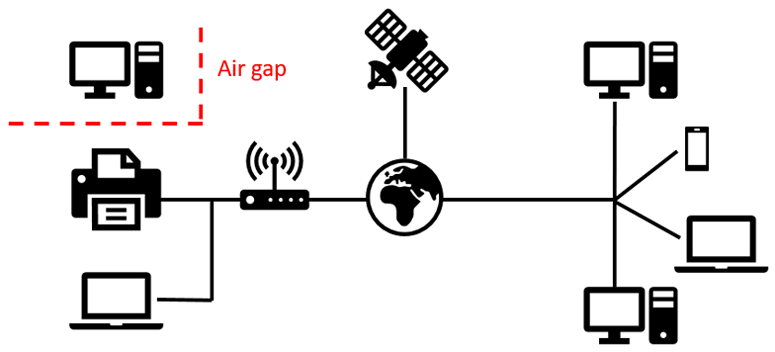
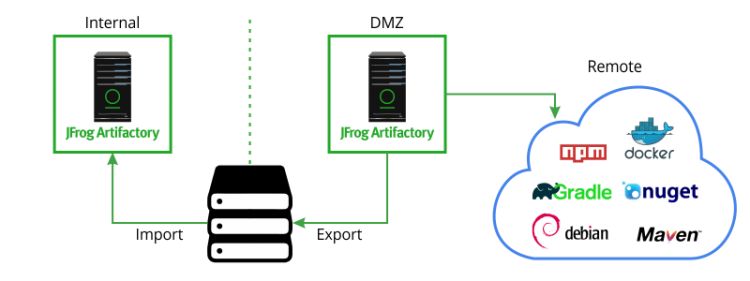
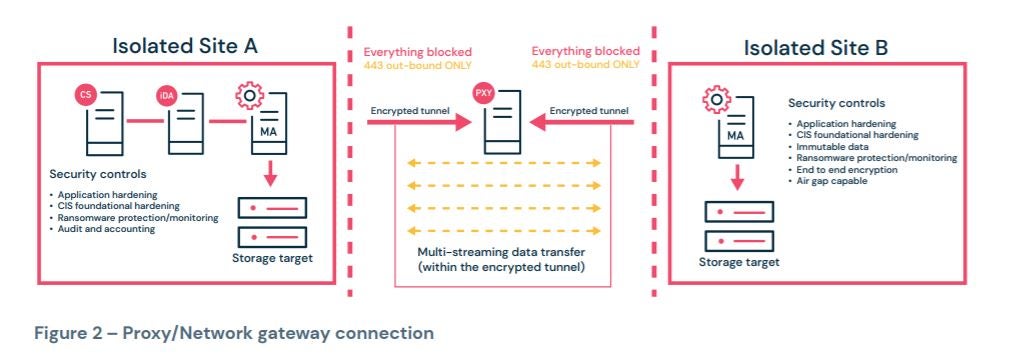
Manual air gap check after re-installation of the inferior half-cover... | Download Scientific Diagram

Virtual air-gap length variation along the machine circumference due to... | Download Scientific Diagram

Virtual air-gap length variation along the machine circumference due to... | Download Scientific Diagram

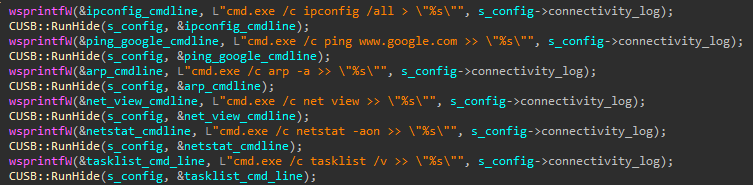
Survey on covert channels in virtual machines and cloud computing - Betz - 2017 - Transactions on Emerging Telecommunications Technologies - Wiley Online Library